firts turn of linux ASLR (Address Space Layout Randomization)
then make vulnerable applications
#include <stdio.h>
#include <string.h>
int main(int argc, char** argv)
{
char buffer[500];
strcpy(buffer, argv[1]); // Vulnerable function
return 0;
}
then compile this scripts and run this applications
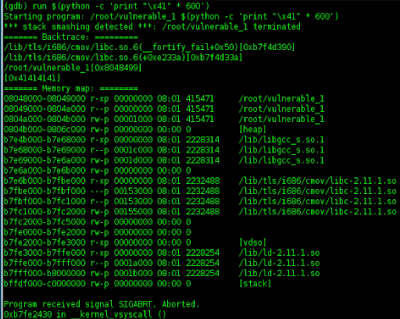
then run fuzzer to make buffer overflow
this showing that gdb have stack smashing protection, to turn off run
then send buffer to overwrite EIP
then check register
this showing that EIP are overwriten by '\x41'
then search ESP address
this showing ESP address is bffff15c, then search address to overwrite EIP with count bffff15c-200 = bffff094 , then make payload
then make fuzzer and run






No comments:
Post a Comment